**The Menace of Malicious PyPI Packages: How Cloud Tokens Were Compromised**
—
In the era of digital transformation, *software development* and *cloud computing* are cornerstones of progress. However, a recent cybersecurity breach involving **malicious Python Package Index (PyPI) packages** has shaken the developer community. These packages were designed to steal cloud tokens and were downloaded more than 14,100 times before their removal. Let’s explore the gravity of this issue and its ramifications on software security.
The Threat Landscape: PyPI Packages and Developer Trust Compromised
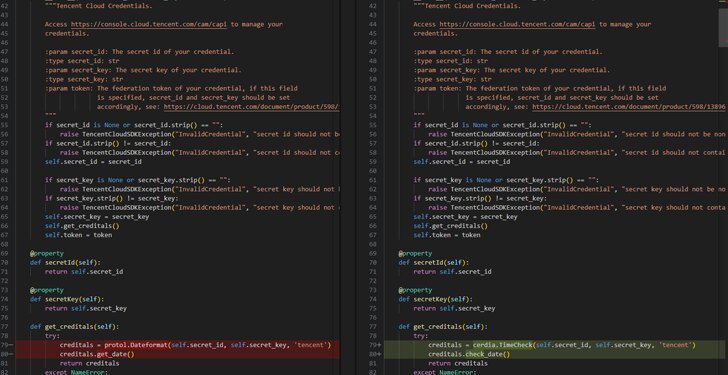
A recent cybersecurity incident revealed several malicious PyPI packages in circulation. These packages were cunningly engineered to pilfer sensitive cloud tokens directly from developer environments, a breach that endangers personal and organizational security.
Understanding the PyPI Ecosystem
The **Python Package Index (PyPI)** is a pivotal repository for Python software packages. Developers turn to PyPI to build, test, and deploy myriad applications. But this incident underscores a critical point: even ostensibly trusted platforms can harbor threats of malicious intent.
How Did the Breach Occur?
The breach exploited a tactic known as **typosquatting**. Malicious packages masqueraded as legitimate software tools, subtly mimicking popular package names to dupe developers. After installation, these packages clandestinely harvested cloud tokens, granting hackers unauthorized access to cloud resources.
Impact and Response
With over 14,100 downloads, the potential fallout is severe. Cloud tokens are access points to sensitive data and crucial applications. When misused, they can lead to:
- Data breaches
- Financial losses
- Reputational damage
Upon detection, the compromised packages were promptly removed from PyPI. Developers were advised to **revoke and rotate their credentials** immediately to mitigate further damage.
Protecting Your Environment: Best Practices
The following best practices can fortify your development environment against similar threats:
- Verify Package Authenticity: Before installation, confirm the legitimacy of a package. Scrutinize the package name, author, and download statistics.
- Regular Security Audits: Conduct periodic audits of your development environment to detect unauthorized packages.
- Use Virtual Environments: Implement isolated environments to confine the impact of potential threats.
- Stay Informed: Follow reliable cybersecurity news outlets for updates on emerging threats and protective measures.
- Implement Strong Credential Practices: Regularly update cloud tokens and use multi-factor authentication wherever feasible.
Conclusion: Staying Ahead in the Cybersecurity Battle
The incident with malicious PyPI packages serves as a powerful reminder: heightened vigilance is imperative within the development community. Adopting robust security measures and staying updated on threat landscapes are critical to safeguarding projects and data.
Let this be a wakeup call for developers worldwide: cybersecurity is a dynamic challenge that demands continuous attention. Secure your coding practices to protect your digital assets against evolving threats. Keep coding diligently, but prioritize coding securely!
Incorporating these strategies can not only enhance your cybersecurity stance but also bolster your project’s integrity against potential incursions. Stay proactive—stay protected.