# Understanding Session Hijacking 2.0: How Cybercriminals are Bypassing MFA in 2024
In the constantly shifting terrain of cybersecurity, hackers are always on the hunt for innovative strategies to circumvent security protocols. A newly emerging technique that has caught the fascination of cybersecurity experts is **Session Hijacking 2.0**. This advanced method offers a novel way for cybercriminals to bypass Multi-Factor Authentication (MFA), a much-revered security measure. Gaining a deeper understanding of this threat is vital for individuals and organizations to fortify their defenses against these crafty cyber adversaries. 🚨
## What Exactly is Session Hijacking 2.0?
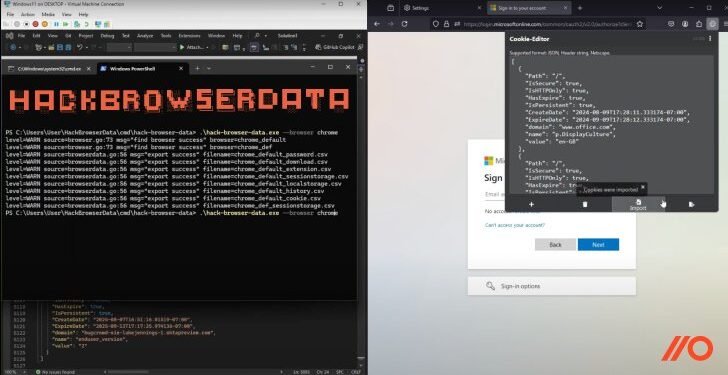
At its core, Session Hijacking involves the interception or takeover of an active user session, enabling unauthorized access to sensitive information or services. The enhanced 2.0 version signifies a quantum leap in this technique, making it a formidable threat. **Session Hijacking 2.0** involves the theft of valid session tokens, which are subsequently used to impersonate legitimate users. This effectively bypasses the layer of security provided by MFA.
**Session tokens** are small data elements designed to verify active sessions. When an attacker acquires these tokens, they can effectively side-step traditional authentication measures, even when MFA is in place. This development raises significant alarm bells, given that MFA has long been hailed as a strong security bulwark.
## How Attackers are Executing Session Hijacking 2.0 🔓
To better understand the mechanics of this modern hacking method, let’s delve into the different techniques cybercriminals are employing:
### Phishing Attacks
– Tailored Phishing Schemes: Phishing remains a go-to tool for cybercriminals. The attack avenues are now customized to extract session tokens instead of just login credentials. Victims are duped into accessing malicious websites, where their tokens are meticulously harvested.
### Man-in-the-Middle (MitM) Attacks
– Data Transaction Interception: During a MitM attack, attackers seamlessly intercept data transactions between the user and the server. Unbeknownst to the user, their session tokens are captured, compromising their security.
### Malware Injections
– Stealthy System Infiltration: Advanced malware has evolved to infiltrate systems unnoticed, collecting session tokens directly without requiring any user interaction.
## The Implications of Session Hijacking 2.0
The fallout from this type of attack transcends financial repercussions. Once infiltrated into a system, attackers can access highly sensitive personal information, intellectual property, or even secure control over critical infrastructure systems. For businesses, a successful breach signifies not just a financial setback but also a substantial loss of customer trust, potential regulatory penalties, and lasting reputational damage.
## Key Strategies for Protection 🛡️
Although Session Hijacking 2.0 seems daunting, there are definitive measures organizations and individuals can take to guard against such intrusions:
### Expiration Policies for Tokens
– Stringent Token Expirations: Implement strict expiration policies for session tokens to significantly reduce the time window available for attacker exploits.
### Endpoint Security Solutions
– Robust Protection Software: Utilize endpoint protection solutions that can detect and neutralize security threats, infusing an additional layer of defense to your systems.
### User Education and Awareness
– Ongoing Training Initiatives: Regular training programs for employees and awareness campaigns for users are indispensable. Educating individuals to recognize phishing attempts and secure personal digital practices can substantially boost security.
### Anomaly Detection Systems
– Behavioral Monitoring Tools: Integrate systems designed to monitor and alert on unusual user behaviors, such as attempts to access resources from multiple locations simultaneously.
### Regular Audits and Updates
– Consistent System Reviews: Conduct periodic security audits and ensure all software remains up-to-date, effectively patching known vulnerabilities to minimize attack surfaces.
## Looking Forward: The Future of Cyber Defense
As cybercriminals persist in their innovative exploits, so too must our cybersecurity strategies evolve. A shift towards adaptive, behavior-based authentication, used in tandem with MFA, could offer a more potent security stance. Cybersecurity frameworks need to continuously develop and adapt, providing proactive defenses against emerging threats like Session Hijacking 2.0.
In conclusion, while Session Hijacking 2.0 poses significant hurdles, understanding its dynamics and ramifications allows for better preparation and defense strategies. Knowledge and vigilance are the starting points in securing sensitive data in our digital age. As we continuously enhance our defenses against such evolving threats, remember: cybersecurity is a field in perpetual flux, demanding our ongoing focus and adaptation. 🛡️💪
This article seeks to inform readers about the latest threats in cybersecurity and offers guidance on how to shield themselves and their organizations from potential breaches. The crux of the matter lies in being informed and implementing proactive strategies to secure the digital landscape. Safe surfing! 🌐