# Uncovering the GCP Cloud Composer Vulnerability: The Risks of Malicious PyPI Packages 🚨
In today’s fast-paced cloud computing landscape, security is non-negotiable. Even the most sophisticated systems can face vulnerabilities, which underscores the evolving nature of cyber threats. Google Cloud Platform’s (GCP) Cloud Composer service recently experienced such a vulnerability, serving as a critical reminder for developers working with cloud services. Here, we delve into the details of this issue and discuss its implications.
## 📚 Understanding GCP Cloud Composer
Google Cloud Platform’s Cloud Composer stands out as a pivotal tool that facilitates the orchestration of workflows across multiple environments—whether cloud-based or on-premises. It leverages the power of Apache Airflow, positioning itself as an integral part of modern data engineering. By managing and scheduling complex data pipelines, Cloud Composer proves indispensable for organizations aiming to streamline their data processing.
## 🚨 The Vulnerability Unveiled
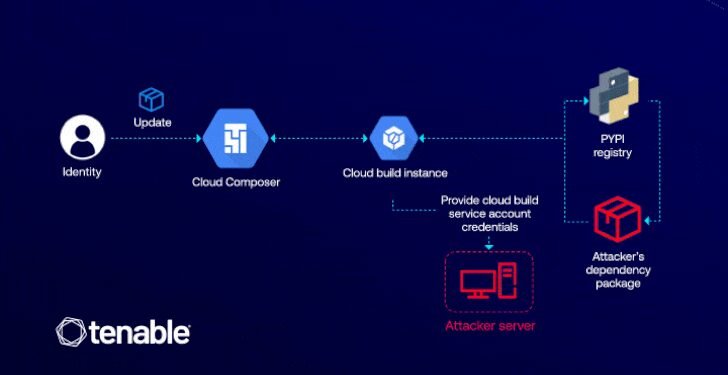
It came to light through the investigations of a security researcher that Cloud Composer was vulnerable to malicious actions involving Python Package Index (PyPI) packages. This vulnerability potentially allowed attackers to escalate their privileges within the GCP environment, risking unauthorized access to critical data and systems.
## 🔎 How the Exploit Works
The crux of the attack lies in the manipulation of Airflow’s dependencies through malicious PyPI packages. When such a package is introduced into the environment, it can execute unintended commands, granting attackers elevated access roles. This nefarious activity ranges from tampering with environment variables to executing high-risk operations threatening the infrastructure’s security integrity.
## 🛡 Why This Matters: Potential Impacts
Security breaches of this type pose severe risks, particularly to organizations that rely heavily on automated cloud workflows and data processing. The potential impacts include:
- Data Breaches: Unauthorized access to data can lead to the leakage of confidential information.
- Operational Disruptions: Altered workflows might disrupt business operations, resulting in downtime and inefficiencies.
- Financial Losses: Breaches often lead to financial damages, negatively affecting both an organization’s bottom line and reputation.
## 🗝 Steps Forward: Mitigating the Risks
In response to the discovered vulnerability, Google quickly patched the flaw and enhanced Cloud Composer’s security features. However, to safeguard against similar threats, organizations must remain proactive. Here are some strategies to reinforce cloud security:
- Regular Updates: Ensure all systems and dependencies are up-to-date with the latest patches.
- Monitor PyPI Packages: Thoroughly vet third-party packages before integrating them into your environment.
- Robust Access Controls: Implement strict privilege management and utilize role-based access controls to minimize harmful access.
- Educate Your Team: Conduct security awareness training to cultivate a culture of vigilance among developers and IT staff.
## 🛠️ Embracing a Secure Future
The unveiling of vulnerabilities like the one in GCP Cloud Composer underscores the ongoing struggle between security professionals and cybercriminals. By adopting proactive measures and adhering to security best practices, organizations can effectively manage these risks, ensuring the safe use of cloud technology.
In conclusion, as technology pushes forward, it brings with it new challenges demanding our attention. Staying ahead involves not only relying on cloud providers to address issues but also actively crafting our own security strategies.
Stay informed, stay secure, and keep innovating! 🚀
This incident serves as a potent reminder of the vital role cybersecurity plays in our increasingly digital world. Understanding these threats and planning accordingly not only safeguards our data but also secures the future of our businesses. How do you plan to protect your cloud environment from potential threats? Share your thoughts, and let us know how you aim to improve your organization’s security stance.