# How Belarus-Linked Ghostwriter is Deploying Malware via Macropack-Obfuscated Excel Macros 🚩
## The Pervasive Threat of Cyber Espionage 🛡️
In the ever-evolving landscape of cyber threats, the emergence of sophisticated espionage tactics signifies growing challenges for cybersecurity experts. Among the most recent developments is the activity of Ghostwriter, a hacking group with links to Belarus, which has upped the stakes in their cyber incursions by utilizing advanced obfuscation techniques. This approach not only intensifies the difficulty for standard security mechanisms to detect malicious operations but also highlights the necessity for both organizations and individuals to be acutely aware and prepared.
## Decoding the Macropack Menace 🎩
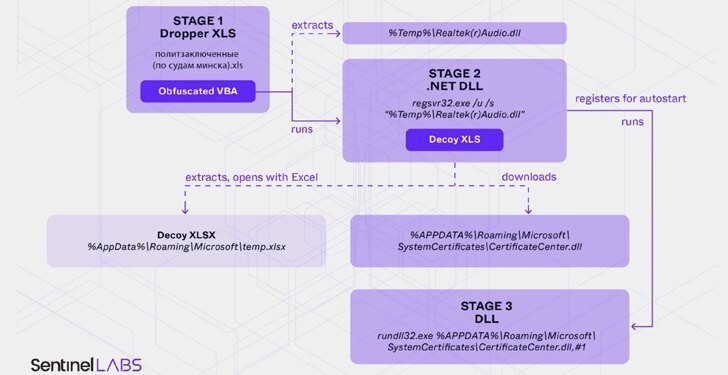
Ghostwriter’s latest modus operandi involves the use of Macropack, a powerful tool that shrouds harmful code within Excel macros. These **automated scripts** are often leveraged to expedite various tasks but are susceptible to exploitation by cybercriminals eager to execute malicious activities discreetly. By cleverly obfuscating the macros, Ghostwriter circumvents many conventional security defenses designed to intercept and neutralize such threats.
### The Deceptive Simplicity of Excel Files
A crucial characteristic of Ghostwriter’s strategy is the deceptive nature of their weaponized Excel files. Disguised to appear as ordinary business documents, these files circulate with an air of legitimacy. Unsuspecting users, upon opening the document, may be prompted to enable macros—a decision that, unbeknownst to them, releases the concealed malware into their systems. This seamless integration of malware into day-to-day operations underscores a serious vulnerability in traditional cybersecurity practices.
## Understanding the Cybersecurity Implications 🔍
This latest revelation from Ghostwriter reflects an alarming trajectory towards stealthier and more effective cyberattacks. The adoption of Macropack-obfuscated macros signals a call to action for beefed-up security protocols across all organizational and personal digital interfaces.
### The Call for Enhanced Security Measures
Herein lies an essential lesson for organizations:
– **Educate and Train Staff:** Regular training sessions should emphasize a culture of skepticism toward enabling macros and enlighten teams about the nuances of phishing tactics and stealth malware.
– **Implement Advanced Detection Tools:** Incorporating innovative security software that can recognize and counter obfuscation techniques is indispensable.
– **Adopt Preventive Strategies:** Simple yet significant practices, such as default disabling of macros and utilizing sandboxing for processing untrusted documents, can substantially mitigate risks.
## Proactive Defense Against Ghostwriter’s Infiltration 🚫
To safeguard against such under-the-radar tactics, consider the following guidelines:
1. **Audit the Source:** Exercise caution by verifying the origin of any document, especially those that request the activation of macros.
2. **Maintain Software Rigor:** Regularly updating antivirus programs and applying the latest security patches ensures your tools are equipped to handle emerging threats.
3. **Foster Cyber Awareness:** Empower your teams with knowledge through continuous education on identifying phishing schemes and recognizing dubious attachments.
The adaptive strategies employed by Ghostwriter must serve as a stark reminder across the cybersecurity domain. As attackers become more technologically savvy, the responsibility lies with each of us to stay informed and implement strategic, preventive actions to protect our digital ecosystems.
## The Ongoing Cybersecurity Battle 🚀
Navigating the cyber world requires constant vigilance and a proactive mindset. As shown by Ghostwriter’s activities, the threats are not only persistent but are evolving in sophistication. This landscape demands dynamic defensive measures and the continuous exchange of knowledge.
### Embracing the Challenge with Knowledge and Innovation
The road ahead will require a collective effort characterized by:
– **Embracing Advanced Technological Solutions:** Keeping pace with the latest cybersecurity innovations is key.
– **Fostering an Informed and Cohesive Community:** Sharing insights and learning from shared experiences strengthens overall resilience.
In conclusion, while the dangers posed by tools like Macropack highlight the pernicious nature of modern cyber threats, our defenses rest in the power of vigilance, education, and strategic preparedness. By enhancing our security posture, we effectively arm ourselves against the complex challenges of today’s digital landscape.
Stay vigilant, stay informed, and remember—**security is everybody’s business!** 🛡️✨