# Unveiling the Bybit Heist: How North Korean Hackers Exploited a Safe{Wallet} Supply Chain Vulnerability 🚨
In the rapidly evolving domain of cryptocurrency, the fine line between prosperous fortune and disastrous catastrophe is often susceptible to breaches by cybercriminals. The crypto world was recently shaken by a monumental security breach at Bybit, a revered cryptocurrency exchange platform. Investigative reports have disclosed that the roots of this high-profile hack lie in a supply chain attack on Safe{Wallet}, orchestrated by the enigmatic North Korean hacking collective. This breach starkly underscores the vulnerabilities inherent in the blockchain ecosystem, vulnerabilities that tech aficionados and crypto investors alike must vigilantly address.
## The Intricacies of the Bybit Security Breach 🔍
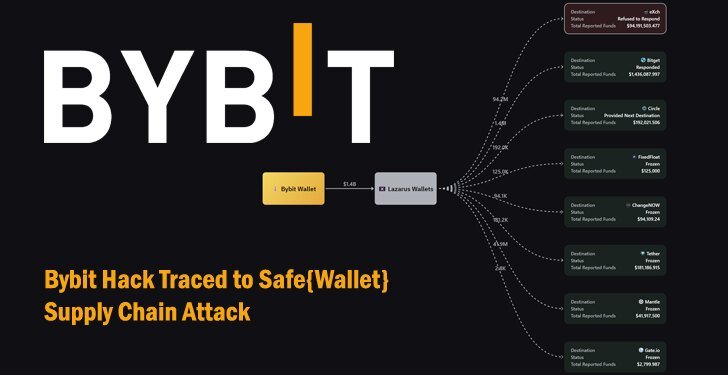
In early February 2025, a wave of panic swept through Bybit users upon learning of unauthorized system access, resulting in considerable financial losses. The unraveling story gained complexity when forensic investigators traced the breach back to an unsuspected vulnerability in Safe{Wallet}. The malicious actors had successfully infiltrated the software supply chain, embedding backdoors that were later exploited by hackers.
## Safe{Wallet} Supply Chain: The Achilles’ Heel 🛡️
Supply chain attacks represent sophisticated cyber threats aiming at software development processes. They enable hackers to insert malicious code during the product development or update phases. This was precisely what transpired with Safe{Wallet}, a trusted digital wallet solution that assists countless Bybit users in safeguarding their crypto assets. The hackers leveraged these backdoors to gain unauthorized access to sensitive user credentials, thereby compromising numerous accounts on the Bybit platform.
## The Role of North Korean Hackers in the Attack 🌐
The investigation into this breach unveiled the involvement of the notorious North Korean hacker group, Lazarus. Known for their technical prowess and unique operational methods, this group has been linked to several high-profile cyberattacks targeting financial institutions. The attack on Safe{Wallet} and the subsequent breach of Bybit emblematizes their strategic approach to infiltrating the cryptocurrency sector, likely providing funds to sustain the country’s initiatives amidst global sanctions.
## Learning From the Attack: Strengthening Crypto Defenses 🔒
With each breach emerges an opportunity for learning and fortification. Here are pivotal measures to bolster cybersecurity within the crypto sphere:
– **Routine Audits and Penetration Testing:**
Regular audits and testing can help identify security vulnerabilities, ensuring that such breaches are mitigated before being exploited.
– **Enhanced Supply Chain Security:**
Firms should implement rigorous third-party risk management strategies to safeguard the integrity of their software supply chain.
– **Decentralization and Encryption Protocols:**
Advanced encryption and decentralized architectures can offer an additional security layer robust against potential infiltrations.
– **User Education and Awareness:**
Continuous education on secure digital practices empowers users to protect their assets proactively.
## Moving Forward: Building a Safer Crypto Ecosystem 🌐
The recent Bybit hack starkly highlights the relentless efforts needed to protect digital assets in the cryptocurrency era. As cyber threats continue to evolve, the vigilance, agility, and resilience of crypto exchanges and stakeholders must evolve concurrently. This incident serves as a profound reminder of the necessity for continual advancements in encryption, security protocols, and user education to safeguard the future of digital finance.
In an arena driven by technology and innovation, maintaining the integrity and trustworthiness of cryptocurrency platforms is paramount. By acknowledging vulnerabilities and enhancing defenses, we can forge a more secure environment for all crypto enthusiasts and investors. Stay informed, stay secure, and guard your digital treasures against lurking cyber adversaries.