Security
Crypto Crisis Unveiled: The $137M TRON Heist by North Korean Hackers 🚨💰
## How North Korean Hackers Exploited TRON Users: A $137M Crypto Heist in a Day 🚨💰 In a shocking turn...
Read more🌐 Unmasking Cyber Espionage: How Iran’s MURKYTOUR Malware Threatens Israel’s Job Seekers! 🚀💼
# Cyber Espionage Unveiled: Iran-Linked Hackers Deploy MURKYTOUR Malware in Sophisticated Phishing Attacks on Israel In today's intricate world of...
Read more🚨 Unmasking the Threat: How Russian Hackers Exploit Microsoft OAuth to Target Allies of Ukraine on Messaging Apps 🚨
# 🚨 Russian Hackers Exploit Microsoft OAuth to Infiltrate Ukrainian Allies via Signal and WhatsApp 🚨 --- ## Introduction In...
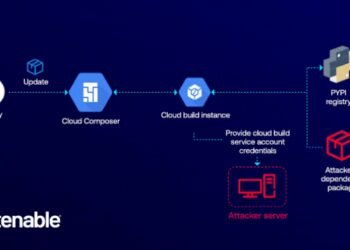
Read more“🚨 Battling Cyber Threats: The GCP Cloud Composer Vulnerability Exposed! 💻🔒”
# Uncovering the GCP Cloud Composer Vulnerability: The Risks of Malicious PyPI Packages 🚨 In today's fast-paced cloud computing landscape,...
Read moreNavigating Digital Security: Why Device Management is NOT the Same as Device Trust! 🔒💻✨
Understanding the Difference: Device Management vs. Device Trust 💻🔒 In the fast-paced realm of digital security, distinguishing between device management...
Read moreGuarding Your Cloud: Combatting AI-Driven Threats to Your SaaS Security 🚀🔒
# Unveiling Hidden Threats: Safeguarding Your SaaS from AI-Driven Breaches 🚀 In today's dynamic digital landscape, Software as a Service...
Read moreSecure Your Digital Kingdom: 🛡️ Unlocking the Power of Blockchain & Strong Passwords 🔑✨
# Protect Your Digital Assets: The Role of Blockchain and Password Security In an age where technology intertwines seamlessly with...
Read more🚫✨ How Google Blocked 5.1 Billion Harmful Ads: A Game-Changer for Online Safety in 2024! 🚀🌐
How Google Tackled the Ad Apocalypse: Blocking 5.1 Billion Harmful Ads in 2024 In the rapidly evolving landscape of online...
Read moreUnmasking the AI Threat: How Gamma is Fueling a New Era of Phishing Attacks on Your SharePoint! 🚨🛡️
Gamma AI Exploited in Elaborate Phishing Scheme: What You Need to Know to Protect Your SharePoint Logins 🚨 In an...
Read moreSupply Chain Security in the Digital Age: Conquering Cyber Threats & Tariff Trials 🚀🔐
# Navigating Modern Supply Chain Challenges: Cyber Threats from Vendors to Tariffs 🚚🔒 In today’s rapidly evolving business landscape, supply...
Read more









































![[Webinar] AI Is Already Inside Your SaaS Stack — Learn How to Prevent the Next Silent Breach](https://biztoplocation.space/wp-content/uploads/2025/04/1745978442314-350x250.jpg)















