Security
🛡️ Beware of Job Scams! North Korean Hackers Target Developers with Deceptive Interviews 💻💼
# Beware: North Korean Hackers Launching Fake Interview Scams to Spread Cross-Platform Malware In today's ever-changing digital world, staying ahead...
Read moreStrengthening Your Digital Fortress: How to Secure Social Media for SaaS Success 🔒🌐✨
## Understanding the Crucial Role of Social Media in SaaS Security In today's digital-first business landscape, social media serves as...
Read moreNavigating the Cyber Storm: How File Hosting Services are Fueling BEC Email Scams 🌩️🔍📧
**Unmasking Cyber Threats: Microsoft's Insight on the Rise of File Hosting in Email Scams 🤖📧** In today's fast-paced digital world,...
Read more🔍 Beware the GoldenJackal: Unveiling a New Era of Cyber Threats to Embassies! 🕵️♀️💻
## **Unmasking GoldenJackal: A New Cyber Threat to Embassies and Secure Systems** --- In the realm of cybersecurity, new threats...
Read moreUnlocking Tomorrow: The Rise of Passwordless Security & MFA Revolution! 🔑✨
# Embrace the Future: Understanding MFA, Passwords, and the Passwordless Revolution 🚀 In today's ever-changing digital world, **secure authentication methods**...
Read moreUnmasking Cyber Resilience: How Cloudflare Defeated a 3.8 Tbps DDoS Titan! 🌐⚔️
# How Cloudflare Successfully Thwarted the World's Largest 3.8 Tbps DDoS Attack 🌍💥 In an era where digital threats loom...
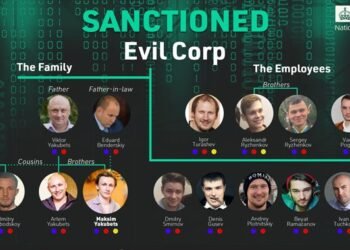
Read moreJustice Served in Cyberspace: The Global Crackdown on Ransomware 🕵️♂️🌍✨
# Global Victory Against Cybercrime: Arrests and Sanctions on LockBit Ransomware and Evil Corp Members 🌐🔒 The digital landscape often...
Read more🚨 Warning: 700,000 DrayTek Routers at Risk! Is Your Network Safe? 🛡️🔒
# 🚨 Protect Your Network: Over 700,000 DrayTek Routers Vulnerable to Hacking with 14 New Security Issues 🚨 ## The...
Read moreCyber Alert! 🚨 How to Shield Your Business from the Devastating CosmicSting Exploit 🛡️🌌
Protect Your Business: CosmicSting Exploit Targets Adobe Commerce and Magento Stores 🚨 In the rapidly evolving landscape of digital retail,...
Read moreTop 5 Essential Tools for Cybersecurity Champions: Master Dynamic Malware Analysis! 🛡️🔍✨
Unlocking Cybersecurity: Top 5 Tools for Mastering Dynamic Malware Analysis 🚀 In an era where digital transformations are rapid, and...
Read more