Security
🚨 Protect Yourself: How Malvertising is Targeting Facebook Users with SYS01stealer Malware! 🛡️🌐
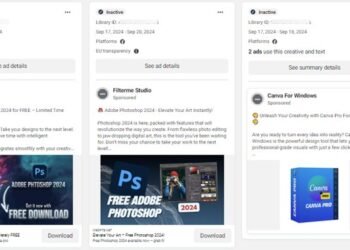
# 🚨 Beware: Malvertising Campaign Targets Facebook Users to Spread SYS01stealer Malware 🚨 In the rapidly transforming world of cyber...
Read moreSmooth Sailing on Your Compliance Journey: Unlock Cybersecurity Success with Intruder! 🚀🔒
# Navigating Your Compliance Journey: How Intruder Elevates Your Cybersecurity Strategy 🚀 In today’s rapidly changing digital world, safeguarding your...
Read more🚀 Navigate the Cyber Minefield: Essential Updates & Tools for Your Digital Security! 🛡️✨
Stay Ahead of Cyber Threats: THN's Weekly Cybersecurity News Highlights & Tools In today's fast-evolving digital landscape, staying updated on...
Read moreUnmasking the Threat: How Malicious RDP Files Are Targeting Ukrainian Entities 🚨🛡️
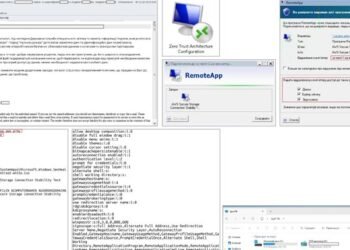
# Safeguarding Ukrainian Entities: CERT-UA Unmasks Malicious RDP Attack Tactics 🚨🔒 In today's digital age, cyber threats are a persistent...
Read more🌟 Unmasking Qilin.B Ransomware: The New Threat You Can’t Afford to Ignore! 🚨
Unveiling the New Qilin.B Ransomware: Enhanced Encryption and Sophisticated Evasion Techniques In an age where digital threats are perpetually evolving,...
Read moreUnlocking the Future of Identity Security: Insights You Can’t Afford to Miss in 2024! 🔒✨
Understanding the Future of Identity Security in 2024: Key Insights from the Latest Permiso Report In today's digital age, protecting...
Read moreNavigating the Dark Side of Ransomware: How LockBit’s Infamy Fuels Fear Tactics 💻💀
# How Ransomware Gangs Exploit LockBit’s Reputation to Strike Fear Into Their Victims ## Capitalizing on LockBit's Demonic Reputation In...
Read moreUnmasking Cyber Shadows: How Gophish Fuels Phishing Attacks with Remote Access Trojans 🔍🚫
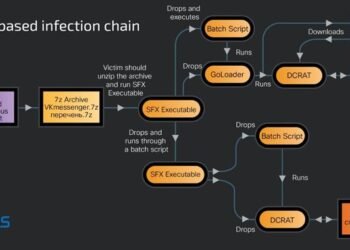
# How the Gophish Framework Powers Dangerous Phishing Campaigns to Spread Remote Access Trojans 🚨 In the ever-evolving world of...
Read moreUrgent Alert! 🚨 Uncovering the Critical Security Flaw in Styra OPA Exposing Your NTLM Hashes 🛡️
# Shield Your Systems: Critical Security Flaw in Styra’s OPA Exposes NTLM Hashes 🛡️ In today’s rapidly evolving landscape of...
Read moreUnlocking Your Cybersecurity Fortress: The Ultimate Penetration Testing Checklist! 🔐🚀
The Comprehensive Penetration Test Checklist for Strengthening Full-Stack Security In the rapidly evolving digital landscape, ensuring robust security across every...
Read more