Security
Watch Out, Cat Lovers! 🐾 The Sneaky GootLoader Malware Targeting Your Bengal Cat Searches in Australia! 🖥️💻
# Beware of the New GootLoader Campaign: A Risk for Cat Lovers Searching Bengal Cat Laws in Australia 🐾🖥️ In...
Read moreTransform Your Cybersecurity Training: How Storytelling Can Make It Unforgettable! 📖✨
# Transforming Cybersecurity Training with Storytelling: Enhance Engagement and Efficacy 🚀 In today’s rapidly evolving digital landscape, cybersecurity has become...
Read more🚨 Don’t Get Caught Off Guard: CISA’s Urgent Alert on Palo Alto Networks Vulnerability! 🛡️✨
# Urgent CISA Alert: Guard Against the Exploitation of Palo Alto Networks' Vulnerability 🚨 In the rapidly evolving realm of...
Read moreUnmasking ‘Fabrice’: The Sneaky Python Package Targeting Your AWS Keys! 🔍🔑🐍
# Discovering 'Fabrice': A Malicious PyPI Package Targeting Developers' AWS Keys 🔑🐍 In the ever-evolving realm of cybersecurity, vigilance is...
Read moreCanada Hits Pause on TikTok: What This Means for Users & Security! 🇨🇦🚫✨
Why Canada’s Decision to Ban TikTok is Making Headlines – What You Need to Know! 🇨🇦🔒 In a groundbreaking decision...
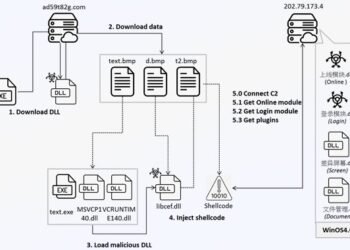
Read moreWatch Out Gamers! 🚨 Unmasking the Winos 4.0 Malware Hiding in Game Optimization Apps 🎮🛡️
# Unveiling the Threat: Winos 4.0 Malware Targets Gamers Through Sketchy Apps 🎮🛡️ In the dynamic realm of cybersecurity news,...
Read more🚨 Urgent Alert for Synology Users: Protect Your Data from a Sneaky Zero-Click Hack! 🛡️
# 🚨 Synology Users Alert: Immediate Patch Required for Zero-Click RCE Vulnerability in NAS Devices 🚨 In the ever-evolving landscape...
Read more🚨 Stay Ahead of Cyber Threats: Essential Tools & Tips for Digital Security 🛡️✨
Essential Cybersecurity Highlights: Top Threats, Tools, and Practices (Oct 28 - Nov 03) In our increasingly digital world, the importance...
Read more🚨 Cyber Alert: 15,000 Credentials Leaked & 10,000 Repositories at Risk! 🔐 Don’t Miss This Critical Update!
# Massive Git Config Breach: 15,000 Credentials Exposed & 10,000 Repositories Cloned! In a disconcerting revelation that has sent shockwaves...
Read moreStay One Step Ahead: Guard Your iPhone Against the New LightSpy Spyware Threat! 📱🛡️🔍
Protect Your iPhone: Understanding the New LightSpy Spyware Threat 📱🔍 In the dynamic, fast-paced world of cyber threats, today's vigilant...
Read more