Security
🚨 Don’t Fall for Cracked Software: Protect Yourself from the New Lumma and ACR Stealer Malware! 🛡️
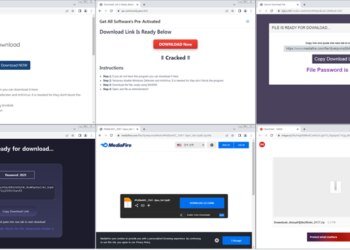
# Beware of New Cyber Threat: Cracked Software Leading to Lumma and ACR Stealer Infections 🚨 In the rapidly evolving...
Read moreApple’s iCloud Dilemma: Privacy vs. Security in the UK 🔐🇬🇧 What You Need to Know!
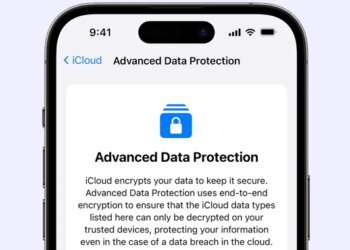
## Apple Faces Cybersecurity Challenges: iCloud's Advanced Data Protection Halted in the UK 🇬🇧🔐 In a notable and unexpected shift,...
Read more🚨 Shield Yourself from Cyber Predators: North Korean Hackers’ Job Scams Target Freelance Developers! 🚀
Beware: North Korean Hackers Are Targeting Freelance Developers with Job Scams to Spread Malware 🚨 The landscape of cybersecurity threats...
Read moreSecure Your Digital Future: Microsoft Patches Critical Vulnerability in Power Pages! 🚀🔒
Safeguarding the Digital Realm: Microsoft’s Patch for Power Pages Vulnerability In today’s constantly shifting cybersecurity landscape, staying vigilant is not...
Read moreProtect Your Privacy: Guarding Against Malicious QR Code Attacks on Signal 📱🔒
**Secure Your Signal Account: How to Protect Against Malicious QR Code Attacks 🚨** In the rapidly changing landscape of cybersecurity,...
Read more🌐🛡️ Unmasking the Snake: How a New Keylogger Variant Slithers Past Security!
# 🐍 Beware: The New Snake Keylogger Variant That Uses AutoIt Scripting to Stay Hidden In today's digital landscape, cyber...
Read more🚨 Beware Mac Users: How to Outsmart the Sneaky FrigidStealer Malware! 🛡️🍏
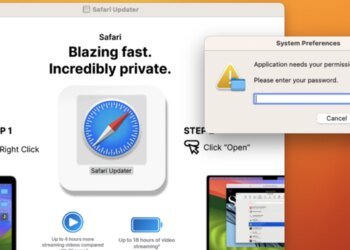
# Beware MacOS Users: FrigidStealer Malware is Targeting You Through Fake Browser Updates 🚨🖥️ --- In today's rapidly changing world...
Read more🦠 Beware of the XCSSET: The Sneaky New macOS Malware You Must Know About! 🚨
Unmasking the New XCSSET macOS Malware Variant: What You Need to Know In today's rapidly advancing digital era, vulnerabilities are...
Read moreNavigating the AI-Powered Landscape of Social Engineering: Strategies to Stay Ahead! ⚙️🤖🔒
## Harnessing AI in Social Engineering: Tools, Techniques, and Precautions ⚙️🤖 In today's digital universe, the realm of cyber threats...
Read moreUnmasking the RA World Ransomware Attack: A Deep Dive into Cyber Espionage and Global Security 🌐🔍💣
**Uncovering the RA World Ransomware Attack: Linking Cyber Espionage in South Asia to Chinese Toolsets 🇨🇳💻** Introduction In a chilling...
Read more