Security
🚨 Uncover the Hidden Danger: Critical Vulnerability in NetApp SnapCenter Exposed! 🛡️💻
Protect Your Data: A Critical NetApp SnapCenter Flaw Could Grant Remote Admin Access 🚨 In the fast-paced and ever-evolving landscape...
Read more🚨 Stay Safe Online: Google’s Urgent Chrome Update & Its Espionage Connection 🔒🕵️♂️
**🚨 Zero-Day Alert: Google's Urgent Chrome Patch and Its Connection to Russian Espionage 🕵️♂️💻** In the ever-evolving domain of digital...
Read moreGlobal Cybercrime Crackdown: INTERPOL’s 306 Arrests & 1,842 Devices Seized! 🌍🔒
INTERPOL's Massive Cybercrime Operation: 306 Arrests and Nearly 2,000 Devices Seized 🌍🔒 In a landmark initiative for international digital security,...
Read moreMastering the Art of Password Protection: Secure Your Data Without the Hassle! 🔑🛡️
# Unlocking the Perfect Balance: Enhancing Password Security Without Compromising User Experience 🔒✨ In today's digital age, securing our online...
Read more“🔍 Unmasking Cyber Espionage: The Intriguing Story Behind Head Mare & Russian Targets 🚀”
# Unraveling Cyber Espionage: Head Mare's Connection to Twelve and Russian Entity Targeting via Shared C2 Servers 🚀 In the...
Read moreSpyware Exposed: How Six Nations Are Breaching Your Messaging Apps! 🔥📲
# Unveiling the Secrets: Six Nations Using Israeli Paragon Spyware to Hack Messaging Apps 📱🔍 In a world increasingly dominated...
Read moreMastering Compliance: How Continuous Monitoring Can Transform Your IT MSP Game! 🚀✨
Elevate Your IT MSP Game: The Vital Role of Continuous Compliance Monitoring In the fast-paced world of IT Managed Service...
Read moreCybersecurity Under Siege: The Dark Crystal RAT Targets Ukraine’s Defense! 🚨🔒
# Cybersecurity Alert: Dark Crystal RAT Strikes Ukrainian Defense with Malicious Signal Messages --- In a rapidly evolving digital age,...
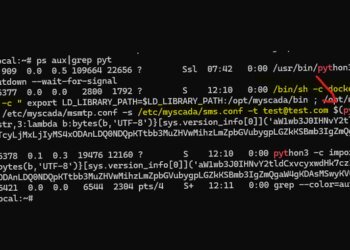
Read moreProtecting the Future: How to Secure Your Industrial Control Systems from mySCADA Vulnerabilities 🛡️⚙️✨
Uncovering mySCADA Vulnerabilities: Protecting Industrial Control Systems from Cyber Threats 💻🔒 In today's rapidly evolving digital landscape, cybersecurity remains a...
Read moreUnmasking MirrorFace: 🚨 Discover the New Cyber Threats & How to Protect Yourself! 🔒
# Exploring MirrorFace: China's Cyber Espionage Group Unleashes ANEL and AsyncRAT in New Attacks 🚀 In the ever-shifting landscape of...
Read more