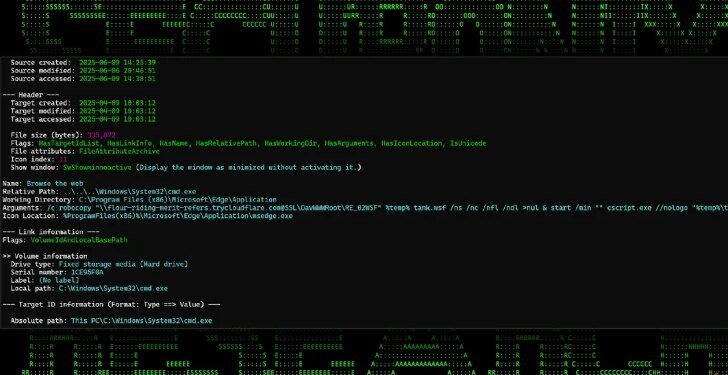
### Unmasking Cloudflare Tunnels’ Role in New Malware Phishing Tactics 🔍
In today’s rapidly evolving landscape of cybersecurity threats, a cunning new malware campaign has emerged. This campaign innovatively harnesses Cloudflare Tunnels to extend its malicious reach, cleverly integrating Remote Access Trojans (RATs) within email-based phishing chains. By exploiting the digital infrastructure trusted by many businesses, cybercriminals are setting a dangerous precedent. Let’s explore the intricacies of this malicious strategy, its potential consequences, and essential actions to shield your systems.
A Closer Look: What Makes This Threat Unique? 🚨
The distinctive aspect of this malware campaign is its strategic use of Cloudflare Tunnels. Traditionally, these tunnels are designed to bolster security by establishing a secure conduit between services. However, cyberactors have managed to repurpose this technology for malicious intent. Leveraging the trusted Cloudflare name, these attackers can disguise their activities under a cloak of perceived legitimacy, making detection significantly more challenging.
Once an unsuspecting victim falls for a phishing email, which might contain an innocent-looking link or attachment, the attackers introduce RATs into the system. These trojans infiltrate quietly, granting the hackers undetected access to sensitive information, shielded by the anonymizing capabilities of Cloudflare Tunnels.
The Dangerous Dance of Phishing and RATs 🎣🔑
Phishing emails remain a perennial weapon in the arsenal of cybercriminals. Their potency increases exponentially when combined with sophisticated tools like RATs. In this malicious operation, emails are meticulously crafted to mimic genuine communications, thereby enhancing the likelihood of the recipient engaging with the malicious link. Following this engagement, the RAT discreetly embeds itself onto the targeted device.
RATs are akin to insidious intruders, stealthily rifling through personal and confidential data, accessing passwords, and even seizing control over webcams or microphones, all without raising suspicion. The potential fallout from such breaches is profound, with repercussions ranging from financial loss, identity theft, or the compromise of proprietary business information.
Protecting Yourself and Your Organization 🛡️
In the face of these emerging threats, it is crucial for both individuals and organizations to reinforce their cybersecurity frameworks. Below are effective measures to enhance your defense strategy:
- Educate: Regular cybersecurity training is paramount. Empower employees with the knowledge to identify and resist phishing attempts, reducing the probability of an attack’s success.
- Verify: Exercise caution by always verifying the sender’s identity, especially when emails encourage opening attachments or clicking on links.
- Security Software: Invest in high-quality anti-virus and anti-malware software solutions capable of detecting and neutralizing threats before any damage can occur.
- Frequent Updates: Regularly updating systems and software is crucial. Updates often include patches for vulnerabilities that cybercriminals could exploit.
- Multi-factor Authentication (MFA): Implement MFA to add an extra security layer, making unauthorized access significantly more challenging.
The Road Ahead: Staying Informed and Vigilant 🌐
As cyber threats continue to become more sophisticated, maintaining awareness is your primary line of defense. Staying up to date with reputable cybersecurity news sources, participating in professional forums, and engaging in conversations surrounding best practices are invaluable for staying ahead of potential threats.
It is essential to remember that while the digital landscape offers numerous opportunities, it also conceals myriad threats. By acknowledging these risks and proactively safeguarding against them, you ensure that your digital defenses remain sturdy and resilient against the ever-evolving tactics employed by cyber adversaries.
—
Stay vigilant and secure, and fortify your digital domain against the stealthy specters of the cyber world! 🌐🔒