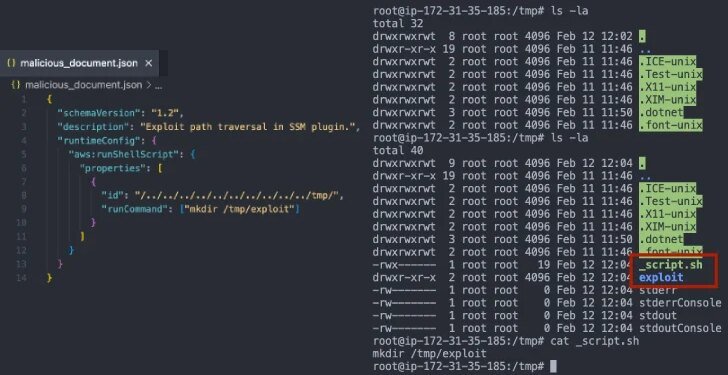
# Amazon EC2 SSM Agent: Crucial Security Patch Addresses Path Traversal and Privilege Escalation Flaws
In the rapidly evolving world of cloud computing, maintaining system security is an ongoing challenge. Recently, Amazon introduced a vital security patch for the EC2 SSM Agent, addressing a vulnerability that could have severe implications if left unpatched. This issue revolves around a path traversal attack, potentially leading to unauthorized privilege escalation. Such vulnerabilities, if exploited, could severely threaten system integrity and data privacy. 🚨
## Understanding the Flaw
Path traversal vulnerabilities represent a significant security weakness. They allow an attacker to access directories and files outside the intended directories, which can result in unauthorized access to sensitive data. With Amazon EC2’s SSM Agent, this could lead to:
– Unauthorized access to sensitive system data
– Manipulation of command executions
– Other malicious activities that compromise system integrity
AWS’s EC2 instances are a cornerstone of their robust cloud computing capabilities. Ensuring their security is critical for any business relying on AWS services. 🔍
## How the Vulnerability Was Discovered
The security of cloud-based services is scrutinized regularly by researchers who play a crucial role in identifying potential threats. In this case, they discovered the path traversal vulnerability in the EC2 SSM Agent and brought it to Amazon’s attention. Once alerted, Amazon acted swiftly to develop a patch that resolves the vulnerability, highlighting the importance of quick and efficient responses to security threats. 🛠️
## Amazon’s Swift Response
Amazon’s rapid deployment of a security patch is a testament to their dedication to protecting user data and system functionalities. For AWS users, updating the SSM Agent is now a top priority to prevent potential security incidents. Regular updates serve as a defense against not only this particular threat but also potential future vulnerabilities. 🔄
## Steps to Secure Your EC2 Instances
To ensure your AWS EC2 instances remain protected, consider the following steps:
- Stay Updated: Regularly check for updates in the AWS Management Console and apply patches as soon as they are released.
- Vulnerability Scanning: Conduct routine security scans to identify potential vulnerabilities early.
- Access Control: Regularly audit and refine user access permissions to enforce the principle of least privilege.
- Education: Keep your teams informed about the latest security practices and potential risks.
- Consult Documentation: AWS provides comprehensive documentation on securing instances and best practices for increasing your cloud infrastructure’s resilience.
## Why It Matters
As businesses increasingly rely on cloud services to drive agility and innovation, the security of these platforms becomes a critical concern. Cloud security breaches can lead to:
– Financial losses
– Reputational damage
– Regulatory penalties
Organizations must remain vigilant and proactive in managing their cloud environments, prioritizing security to guard against such vulnerabilities. This is not merely a technical concern; it’s a business imperative.
## Conclusion
The incident with Amazon’s EC2 SSM Agent serves as a wake-up call about the volatile nature of cybersecurity threats. It underscores the vital role of collaboration between service providers and security researchers in mitigating risks. As technology advances, so does the sophistication of security threats. Staying informed and updated is crucial for enhancing an organization’s overall security posture. 📈
In the digital landscape, vigilance and timely action remain your greatest allies. Stay safe and secure in the cloud. 🌐
—
Looking to stay informed about the latest in cloud security and technological developments? Subscribe to our blog for updates. 📫📢