Understanding the Recent Surge in Cyber Attacks: Chinese Hackers Deploy SNOWLIGHT Malware on Linux Systems
In a concerning development within the realm of cybersecurity, Chinese hackers have been leveraging an aggressive toolkit comprised of the SNOWLIGHT malware and the VShell tool to target Linux systems. This sophisticated attack scheme has sent ripples across the technology sector, highlighting vulnerabilities in systems often deemed more secure than others. Dive with us into the intricate details of this emergent cyber threat and explore the implications for businesses and individuals alike.
The Rise of SNOWLIGHT Malware 🚨
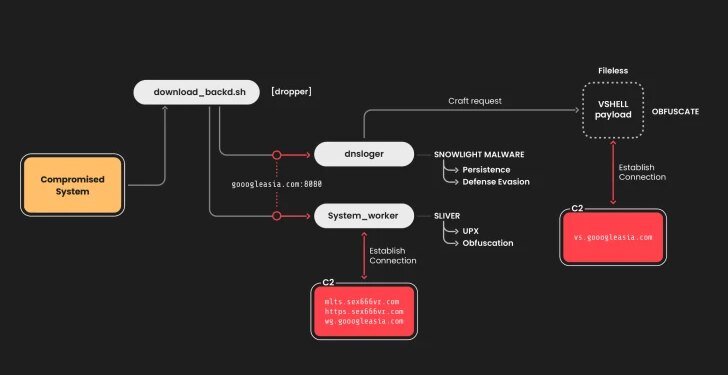
The appearance of the SNOWLIGHT malware is akin to unveiling a new era of cybersecurity challenges. Specifically tailored to infiltrate and compromise Linux systems, SNOWLIGHT provides hackers with the capacity to gain unauthorized access and exert control over networks. A notable aspect of SNOWLIGHT is its ability to camouflage its actions, thereby complicating the efforts of cybersecurity specialists to detect and thwart its operations.
The Role of the VShell Tool 🔑
Traditionally, the VShell tool is employed for secure communication and seamless data transfer. However, hackers have appropriated it to establish clandestine communication channels back to their own command centers. With VShell in their toolkit, attackers can sidestep conventional security measures and surveillance mechanisms, facilitating an undetected foothold in compromised systems.
Why Target Linux Systems? 🤔
Linux enjoys wide adoption in the tech industry owing to its robust performance and open-source nature. Many enterprises have leaned on Linux for managing their servers and critical infrastructure, under the false belief that it is invulnerable to breaches. The advent of attacks like those involving SNOWLIGHT shatters this misconception, underscoring the importance of vigilance and stringent, updated security protocols. Linux systems are not inherently breach-proof, and this campaign serves as a stark reminder of that fact.
Impact on Businesses and Individuals 📉
The ramifications of exposing vulnerabilities on such a scale are substantial for businesses. Unauthorized network intrusions can lead to data breaches, culminating in the loss of sensitive information, tarnished reputations, and dire financial consequences. Additionally, individual Linux users are not immune; the risk of personal data compromise, identity theft, and other personal security threats looms large.
How to Protect Against These Threats 🔐
- Regular Updates: Consistently applying the latest security patches is a cornerstone in combating known vulnerabilities exploited by malware such as SNOWLIGHT.
- Enhanced Security Protocols: Implementing advanced security measures, including firewalls, intrusion detection systems, and encryption, significantly boosts defenses against such assaults.
- Network Monitoring: Diligent monitoring of network traffic can unearth peculiar activities that might signal a breach, allowing entities to respond swiftly.
- Education and Training: Equipping staff and users with knowledge of cybersecurity best practices is critical to maintaining a secure operational environment.
A Call to Action for the Cybersecurity Community 💼
The discovery of the SNOWLIGHT malware campaign serves as a rude awakening for the worldwide cybersecurity community. Collaboration and the sharing of pertinent information are essential for developing comprehensive strategies to counter such advanced threats. By staying informed and adopting a proactive stance, organizations and individuals alike bolster their defenses against the ever-evolving landscape of cyber risks.
This attack is a stark reminder that the digital world is in constant flux, necessitating continual advancements in protective measures. As threats evolve, so must our efforts to safeguard against them. Heightened awareness, robust security protocols, and a community of informed cybersecurity professionals are indispensable in defending our digital assets. Together, we can fortify our defenses and navigate the digital world securely. Stay vigilant, stay protected! 🔒