Uncovering the New Threat: Exploit Bypasses Patched NVIDIA Container Toolkit Vulnerability 🚦
In the dynamic realm of cybersecurity, staying ahead of ever-evolving threats demands unwavering vigilance and a proactive approach. A recent discovery reinforces this requirement as researchers unveil a new exploit that circumvents a previously patched vulnerability in NVIDIA’s Container Toolkit. This post delves into the implications of this discovery for global users and offers strategies for protection.
Understanding the Scope of the Threat
The NVIDIA Container Toolkit is indispensable for those employing containerized applications to harness GPU acceleration. It offers essential tools to build, manage, and optimize GPU-based applications, making it a cornerstone in high-performance computing settings.
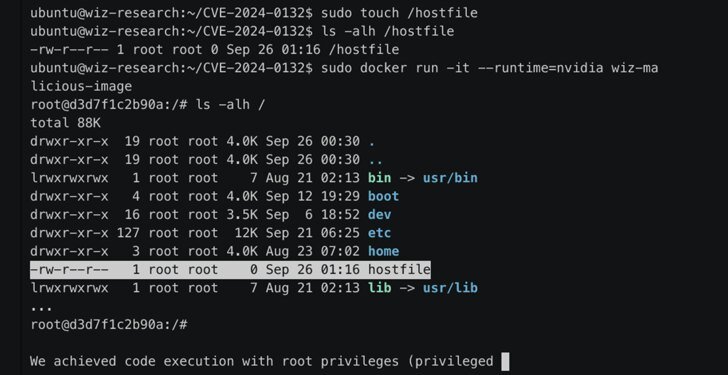
Recently, this toolkit was at the center of a significant security breach. A vulnerability was identified and patched, yet a new exploit has emerged, effectively bypassing the fix and presenting an ongoing threat to users who depend on the toolkit’s integrity. The uncovering of this exploit is a stark reminder that cybersecurity solutions must be as adaptable as the threats they aim to mitigate.
The Exploit Details: What We Know 🕵️♂️
While the intricacies of this exploit remain classified, researchers have highlighted its potential to bypass existing security protocols—revealing a substantial vulnerability requiring immediate attention. This exploit demonstrates an ability to execute arbitrary code, which could lead to unauthorized data access and potential system disruptions.
This discovery underscores the critical nature of an evolving cybersecurity landscape, where threats are perpetually adapting to overcome protective barriers. It poses a direct challenge to environments where the initial patch was considered adequate.
The Implications for Users and Organizations 🔍
For users and organizations deploying NVIDIA’s Container Toolkit, this finding represents a crucial call to action. The exploit poses a potential risk to sensitive data and system stability, particularly in industries that rely heavily on GPU acceleration for applications such as machine learning and data analytics.
Organizations must assess their preparedness and response strategies to mitigate these risks effectively. Understanding the gravity of the threat is important for maintaining operational resilience and integrity.
Mitigation and Recommended Actions 🔒
- Regular Security Updates: Ensure that your systems are consistently up-to-date with patches, not only for the Container Toolkit but for all software components. Maintaining regular updates is critical to mitigating risks and protecting your infrastructure from potential exploits.
- Layered Defense Strategy: Implement a multifaceted cybersecurity strategy that incorporates firewalls, intrusion detection systems, and regular security audits to identify anomalies early.
- Employee Training: Cybersecurity is a human issue as much as it is a technical one. Conduct regular training sessions for employees to help them recognize phishing attempts and other exploit delivery methods.
- Community Engagement: Participate in cybersecurity forums and communities to stay informed about the latest security alerts and strategies. Staying connected and informed can make a significant difference in your cybersecurity preparedness.
A Look Ahead: The Race Against Cyber Exploits 🚀
As researchers work tirelessly to develop more robust solutions against this exploit, the incident serves as a reminder of the continuous challenges in cybersecurity. The field is marked by a persistent race, where defenders and attackers alike are in a constant state of evolution, each aiming to outsmart the other.
Users are encouraged to take proactive measures and nurture a culture of security awareness. This incident highlights that maintaining a secure system is not a one-off task but an ongoing commitment. As updates on this issue develop, it is crucial for users to stay informed and engaged.
The discovery of this exploit in the cybersecurity domain underscores the paramount importance of vigilance. The best defense against the unpredictable landscape of cyber threats remains a combination of regular updates, informed awareness, and layered defenses. Let us stay informed, stay secure, and safeguard our digital spaces together. 🌐🔒